Using secrets in Logic Apps in a secure way
By Anatoly Mironov
This is a guide for how to handle secrets in a logic app in a secure way. It combines three resources:
- Accessing Key Vault from Logic App with Managed Identity
- Get Secrets Key Vault API
- Hide your logic apps secrets from prying eyes

First, enable a Managed Identity for your Logic App:
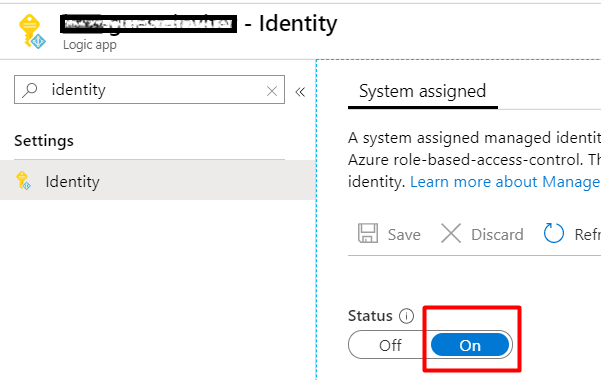
In the KeyVault, add a new Access Policy for the new Managed Identity (from the previous step). Use the least priviliges. In my case it is just enough with GET for secrets.

Next add an HTTP action to the key vault.

The values should be:
- Method: GET
- URI: https://your-key-vault.vault.azurenet/secrets/your-secret
- Query: api-version = 7.0
- Authentication: Managed Identity
- Audience: https://vault.azure.net
Next, open the Settings of the “Get Client Secret” action and tick the “Secure Outputs (Preview)”
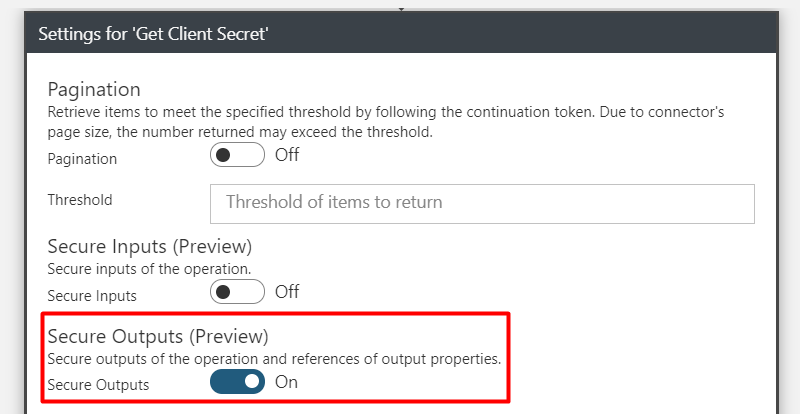
To get the secret we need to parse the http response. Only the value is needed.

Now let’s call the Graph API and authenticate using this secret:
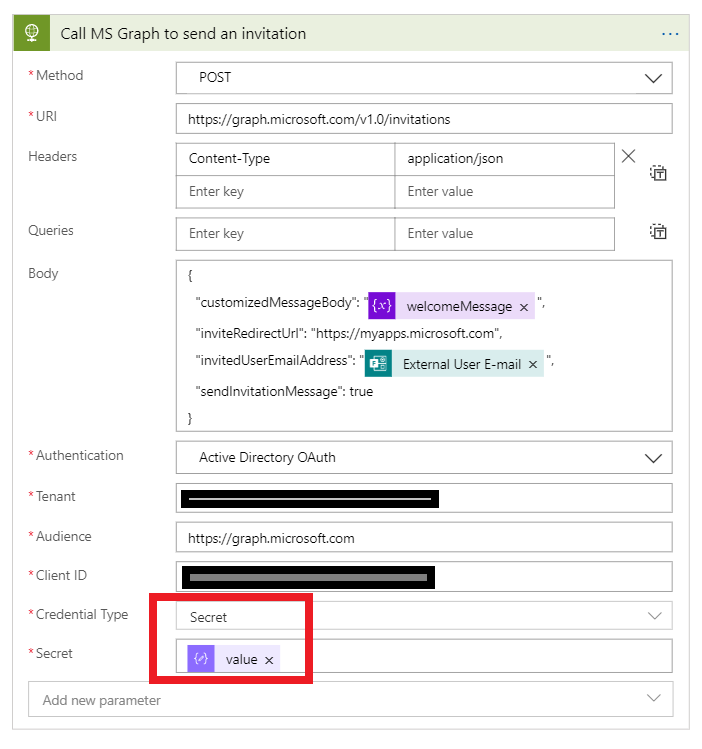
In the run history we can see now, that the password is not shown anymore.

Neither it is visible in the next http call:

Note that the run history is kept for a while, if you have used secrets in plain text, it is a good practice to change them.