What about the SharePoint app domain?
By Anatoly Mironov
This is an open question about the domains for SharePoint apps. On Technet: Configure an environment for apps for SharePoint (SharePoint 2013) we can read the following:
You must configure a new name in Domain Name Services (DNS) to host the apps. To help improve security, the domain name should not be a subdomain of the domain that hosts the SharePoint sites. For example, if the SharePoint sites are at Contoso.com, consider ContosoApps.com instead of App.Contoso.com as the domain name.
Does it apply to SharePoint Online? Well, apparently not :) So why should we do it on premises? 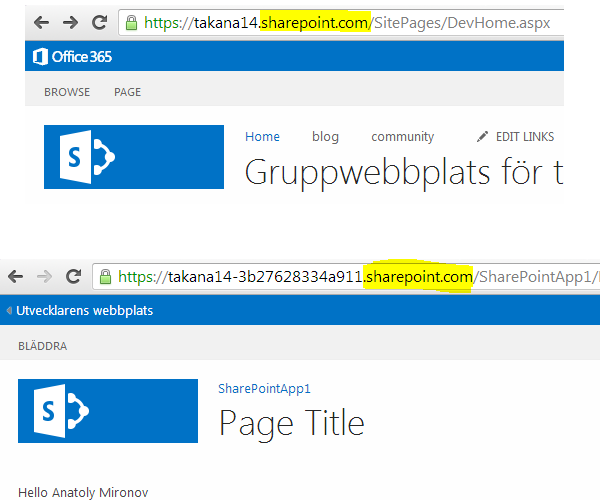 As we all know, sharepoint.com is used for our Office 365 tenancies and for apps.
As we all know, sharepoint.com is used for our Office 365 tenancies and for apps.
Comments from Wordpress.com
Anatoly Mironov - Nov 1, 2014
Thank you for your comment. What I’ve been thinking about is also Yammer. Yammer uses the same domain (not even implementing subdomains) for all companies: yammer.com/companyA, yammer.com/companyB and so on. I am sure they have security tools in place to prevent unathorized access, but in my point of view, and I suppose in yours (google example) it is done in the wrong way in the foundation of the service.
Stuart - Mar 6, 2014
Thanks Anatoly, really interesting
m00ntear - Nov 2, 2014
Well the same-origin policy exists for a reason and I’m not sure why MS does it this way in O365. There is some more information and recommendation here: http://technet.microsoft.com/en-us/library/fp161237%28v=office.15%29.aspx - Take google as an example. Google uses google.com for trusted activities and *.googleusercontent.com for untrusted sites. Read about the cookie security here: http://security.stackexchange.com/questions/12412/what-cookie-attacks-are-possible-between-computers-in-related-dns-domains-exa I really don’t like the custom domain for apps, but everything suggest we really should use it. Would be great if MS would shed some light on how they implemented it for O365.